Gateway and End Nodes
Thing Interaction Framework treats both the gateway and end nodes as things, just like the stand-alone thing (i.e., a thing that will not use the gateway).
In this section, we will explain how to identify things. We will also explain how the things are secured.
Identifiers of the gateway and end nodes
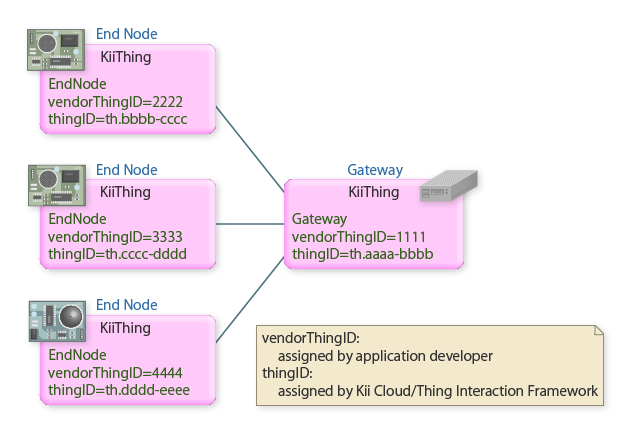
In Thing Interaction Framework, we use two IDs (vendorThingID and thingID) to identify the gateway and end node.
The concept of vendorThingID and thingID is the same as that of the stand-alone thing. See Thing identifier for the details.
The next figure shows an example of connecting three end nodes onto a gateway.
Owner
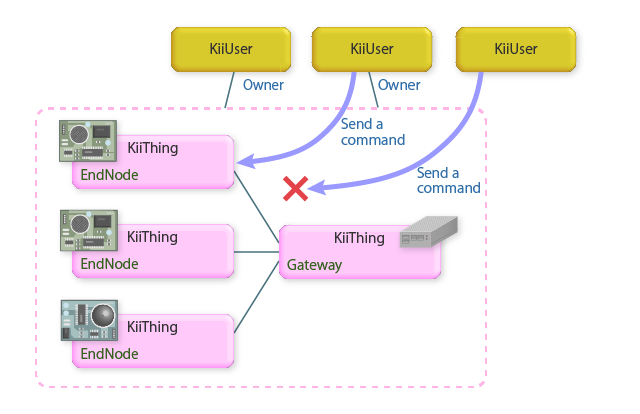
The gateway and end node identify the user (KiiUser) or group (KiiGroup) who will use them as an owner. When onboarding the gateway and end node, you need to bind the owner to them.
The concept of the owner is the same as that of the stand-alone thing. See Thing owner for the details.
An owner will have the privilege to access the gateway and end node they own. They will be able to send commands and browse the states of the things. A user who is not the owner will not be able to access the things. As shown in the figure below, the same owner is usually bound to the gateway and the end nodes that are connected to the gateway.
Access token and security
Just like a stand-alone thing, a gateway and end node will have their own access tokens. The owner will also have their own token. See Access token to learn more about the access token. Thing Interaction Framework determines which user (or thing) is executing the operation by checking the access token set in the request.
The following figure illustrates how the security is preserved with the access tokens. The figure shows the information used to ensure the security of the gateway, end node, mobile application, and owner.
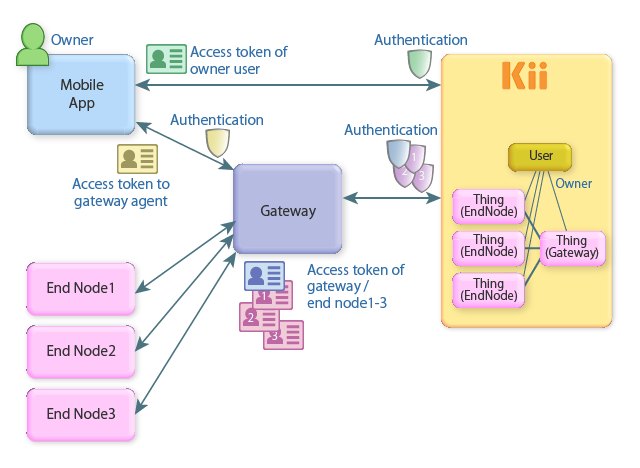
Acess token
Here is a list of tokens appeared in the figure.
Note that the access token of the gateway and end nodes will be processed internally when they are initialized and onboard; to understand the overall security model, it is advised to get the picture of them as well.
The access token of the owner user (in green)
This access token is used when a mobile application accesses Kii Cloud/Thing Interaction Framework on behalf of the owner user. It is issued by Kii Cloud/Thing Interaction Framework.
The mobile application can get the access token by logging in with the owner user's username and password. You can also get the token by creating a pseudo user (Android, iOS, JavaScript, REST).
The access token for accessing the gateway (in yellow)
This access token is used when a mobile application accesses the gateway agent. It is issued by the gateway agent.
The mobile application can get the access token by executing the authentication API of the gateway's local REST API via Wi-Fi. The authentication is to be made with the gateway's password.
The access token of the gateway (in blue)
This access token is used when a gateway accesses Thing Interaction Framework with its own privilege. It is issued by Thing Interaction Framework.
The gateway can get the access token by authenticating with its password upon onboarding itself.
The access tokens of the end nodes (in purple)
These access tokens are used when a gateway accesses Thing Interaction Framework on behalf of the end nodes. They are issued by Thing Interaction Framework and are issued for each end node.
The gateway can get the access token by authenticating with the end node's password when the gateway onboards the end node.
Password
The following passwords are used to ensure the security.
The password of the owner user
This password is used to authenticate the owner when getting their access token. If you use a pseudo user (Android, iOS, JavaScript, REST), you can get the access token without providing any password.
The password is expected to be inputted by the end user as the part of the login information.
The password of the gateway
This password is used for the following two purposes:
- It is used by the mobile application to access the gateway's local REST API. It is used for getting the access token of the gateway agent.
- It is used by the gateway to access Thing Interaction Framework with its own privilege. It is used for getting the gateway's access token.
The password is to be specified when the gateway is installed (i.e., set as the factory default or set upon the gateway installation).
The password of the end node
This password is used to access Thing Interaction Framework with the end node's privilege. You can assign a different password for each end node. The password is used for getting the access token of the end node.
The password is to be specified by the mobile application upon the end node onboarding. The mobile application can ask the end user to type in the password, or it can use the randomly-generated string as the password.
The gateway will use the end node's access token when accessing Thing Interaction Framework, but the end node does not need to share its password with the gateway. The gateway will internally handle the end node's access token.
Please note that Thing Interaction Framework does not secure the communication between the end nodes and converter. Please apply some security measures as needed.