Security
Security consideration is important in the process of mobile app development and operation. This section explains the security in Kii Cloud.
In addition to detailed technical information on security, we provide technical tips for implementing your apps. These tips cover topics like transactions and performance handling. For details, see "Implementation Tips" in the reference guide (Android, iOS, JavaScript, REST).
Kii Cloud security
Here is a list of Kii Cloud security aspects that relate to your mobile app development.
Communication channel security
The communication channel between Kii Cloud and devices is secured with the SSL/TLS protocol. API requests made by Kii Cloud SDK and REST API are made via HTTPS. In addition, the MQTT for IoT can also leverage the SSL/TLS based protocol.
Server security
Kii Corporation is fully responsible for ensuring the security of the server operations, such as setting server permissions and applying security patches. Developers thus do not need any special consideration on the server security. As described in Server Extension, developers are not responsible for any server operation even if they run their custom logic on the server.
Application security
When designing an app that integrates Kii Cloud features, developers need to consider security at the application level. We will explain the basics in the remaining sections of this page.
Application security
For ensuring the security of a Kii Cloud application, the first thing to consider is the security of the data saved by users.
The data saved by mobile apps are designed to be protected by each user's password.
- Data saved in a user scope cannot be accessed by anyone other than the user themselves.
- Data saved in a group scope cannot be accessed by anyone other than the members of the group.
Even if an attacker has knowledge of the application design or has its source code, the attacker cannot access the user's data unless he knows the password of the target user.
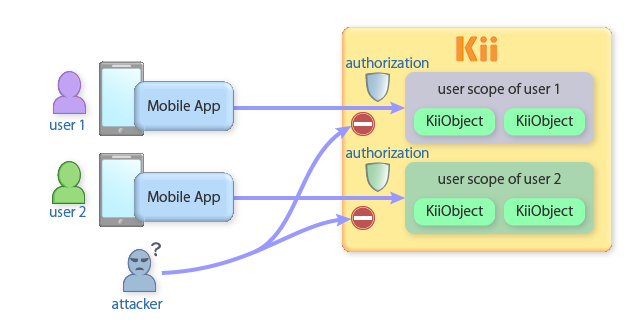
As an open system, Kii Cloud is disclosing the specification for accessing the server to the public. Therefore, an attacker can reproduce the same procedures for accessing the API by decompiling your mobile app. Since each user's data is protected by their password, however, the attacker cannot access the data.
A mobile application that conforms to the basic design model of Kii Cloud will be a secure application. Normally, the mobile app will create a user and store their data in their scope. The data stored with this design will be resilient from attack.
There are other points, besides from storing data, where some security consideration is required. We will provide the corresponding design tips separately in the reference guides.
Comparison with proprietary server
The security of the Kii Cloud is tighter than systems that adopt the "Obfuscated implementation" as the basis of security.
Some people think that a proprietary server that hides its communication specification is safer than an open system like Kii Cloud. This is not true since relying solely on the obfuscated implementation is fairly vulnerable. A motivated attacker can analyze a mobile app without any time limitation and by any means. As long as the attacker can obtain an execution module of your client, the fact that the source code or specification is hidden is trivial.
On the assumption of an open specification, Kii Cloud ensures its security by the user authentication and access authorization mechanisms. As mentioned above, an attacker cannot access user's data even if they know how to access them.
It is possible to achieve the security level equivalent to the Kii Cloud on a proprietary server. A cost for validating and testing the server security, however, tends to be treated less since the security does not directly contribute to the functionality and product values of the final service. Kii Cloud treats the security seriously by regarding the security as a part of its functionality; we conduct sufficient amount of verification and testing for ensuring the security.
Learn more...
- See "Security" (Android, iOS, JavaScript, REST) for the detailed technical information about the security.